Virtual Protection Relays (VPRs) are a modern approach to grid protection that replace traditional, dedicated relay hardware with software running on virtualized servers.
Protective relays have evolved steadily over time. Early power systems relied on electromechanical relays, which were later replaced by solid-state devices and then by microprocessor-based relays. Virtual Protection Relays represent the next step in this evolution, driven by advances in computing power and the ongoing consolidation of hardware.
Rather than installing a separate physical relay for each protection function, VPRs run as software on shared, high-performance servers. A single server can host multiple virtual machines, each running its own VPR. Even though they share the same physical hardware, each virtual relay operates independently, just like a traditional standalone relay.
With this shift, interaction also changes. Instead of front-panel lights, buttons, and physical wiring connections, engineers access and manage VPRs through network-based tools. These include graphical user interfaces (HMIs), browser-based dashboards, and centralized management systems.
A typical VPR system is built using several distinct layers, each with a specific role. In this article, we’ll break down those layers one by one and explain how they work together to form a complete virtual protection relay architecture.
1. Hardware Platform
Virtual Protection Relays rely on general-purpose servers or edge-computing devices that are powerful enough to handle near real-time processing. Even though the protection logic is software-based, the underlying hardware must be robust, reliable, and designed for critical infrastructure.

Physical Requirements
Servers used for VPRs must be suitable for harsh substation environments. These locations can experience electrical surges, wide temperature swings, vibration, and high levels of electromagnetic interference (EMI).
To ensure reliable operation, servers and networking equipment (such as switches, routers, and communication gateways) must comply with industry standards like IEC 61850-3 and IEEE 1613, which define environmental and electrical requirements for substation equipment.
Processor (CPU)
The processor is responsible for running multiple virtual machines at the same time. For this reason, VPR servers require CPUs that support hardware virtualization. High core counts, large internal caches, and support for large amounts of memory are important to ensure each virtual relay has the resources it needs.
In practice, this usually means server-grade processors such as Intel Xeon or AMD EPYC. These processors include built-in virtualization feature, such as Intel VT-x/VT-d and AMD-V/AMD-SVM.
Memory (RAM)
System memory must be highly reliable. Most VPR platforms use ECC (Error-Correcting Code) RAM, which can detect and correct certain types of memory errors automatically.
ECC memory works by storing extra bits of data, called parity bits, alongside normal data. The system continuously checks this information for consistency. If a memory bit unexpectedly changes due to electrical noise or radiation, the ECC logic can identify the error and correct it before it causes a fault or system crash.
Storage
The storage system is also a key part of the platform. Multiple drives should be combined using RAID (Redundant Array of Independent Disks). RAID configurations either mirror data across drives or spread it across multiple disks in a controlled way. This allows the system to continue operating even if one drive fails, eliminating single points of failure and reducing downtime.
Modern servers often use solid-state or NVMe drives because of their high performance and low latency. However, these drives generate heat and gradually wear out with repeated write operations, so proper cooling and monitoring are essential.
Power Supply (PSU)
Power reliability is critical in protection systems. Servers should be equipped with redundant power supplies, meaning more than one PSU is installed. Common configurations include N+1 (one extra supply for backup), 2N (fully independent power paths), and parallel designs where multiple supplies share the load.
If one power supply fails, the remaining unit or units immediately take over without interrupting operation. In hot-swappable designs, a failed PSU can be removed and replaced while the server remains online, ensuring continuous protection system availability.
2. Virtualization Layer
The virtualization layer is what allows multiple protection functions to run on the same physical server while remaining logically separate. This layer creates isolated environments for each protection function, often referred to as virtual IEDs (vIEDs).
There are two main approaches used at this layer: virtual machines (VMs) and containers. The choice between them involves tradeoffs between isolation, performance, and efficiency, but in both cases, the virtualization layer is what makes software-based protection practical and scalable.
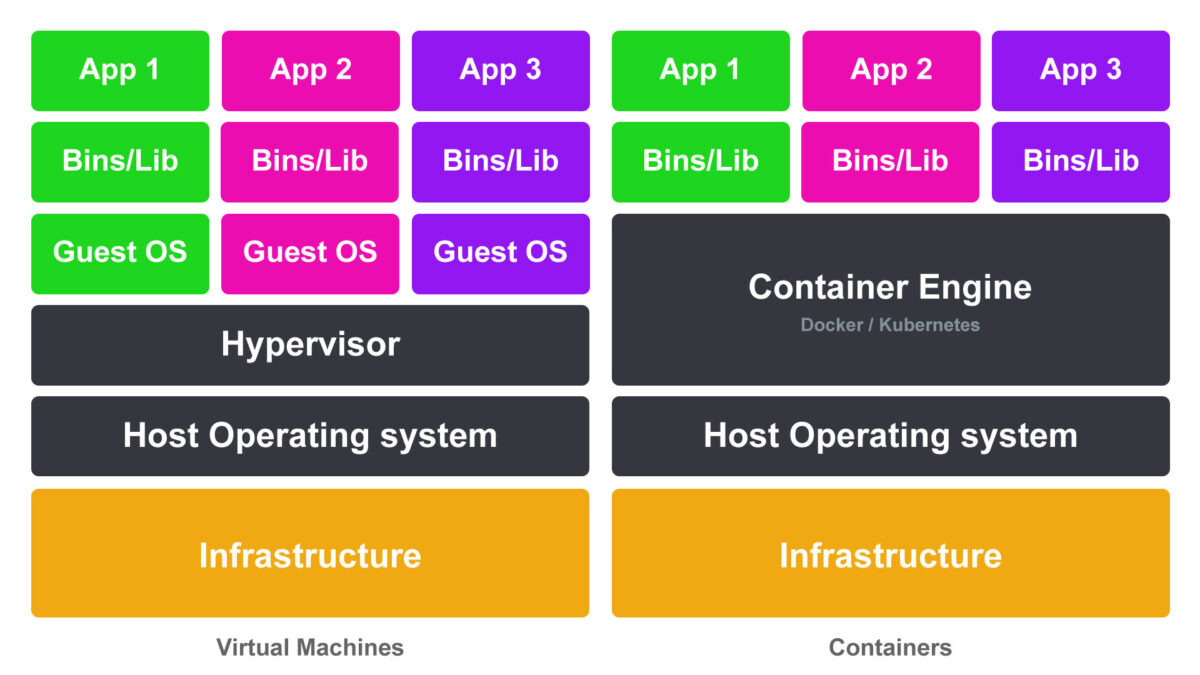
Virtual Machines (VMs)
A virtual machine behaves like a complete, independent computer. Each VM includes its own operating system, along with the protection software running on top of it. This strong isolation makes VMs easy to manage and familiar to many engineers, but it comes at a cost.
Because every VM runs a full operating system, they consume more CPU, memory, and storage resources. Startup times are also longer, since the entire operating system must boot before the protection application can run.
Containers
Containers take a lighter-weight approach. Instead of virtualizing the hardware, containers virtualize the operating system itself. All containers share the host system’s core operating components.
By sharing the operating system, containers are much smaller and more efficient than virtual machines. They start almost instantly, use fewer system resources, and allow a higher number of protection functions to run on the same hardware. Platforms such as Docker and Kubernetes are commonly used to deploy and manage containers at scale.
3. Protection Software
The protection software layer is where the actual grid protection logic lives. This is the digital equivalent of the algorithms that traditionally ran inside physical protection relays.
At this layer, software modules continuously analyze electrical measurements (such as current, voltage, and frequency) from Merging Units (MUs) to identify abnormal operating conditions. These measurements are used to implement common protection functions such as overcurrent, distance, differential, and frequency protection.
Related: Next-Generation Substation Technology: Centralized Protection and Control
Each of these functions runs as a software component within a virtual environment, but from a system behavior standpoint, they operate just like their hardware-based counterparts. They follow the same protection principles, timing requirements, and coordination rules that have been used for decades.
4. Communication Standards
Virtual Protection Relays depend on fast, reliable digital communication to function correctly. Instead of exchanging signals through hardwired connections, VPRs use standardized network protocols to share measurements, commands, and status information. Because protection decisions must be made in milliseconds, these communications must be both predictable and highly redundant.
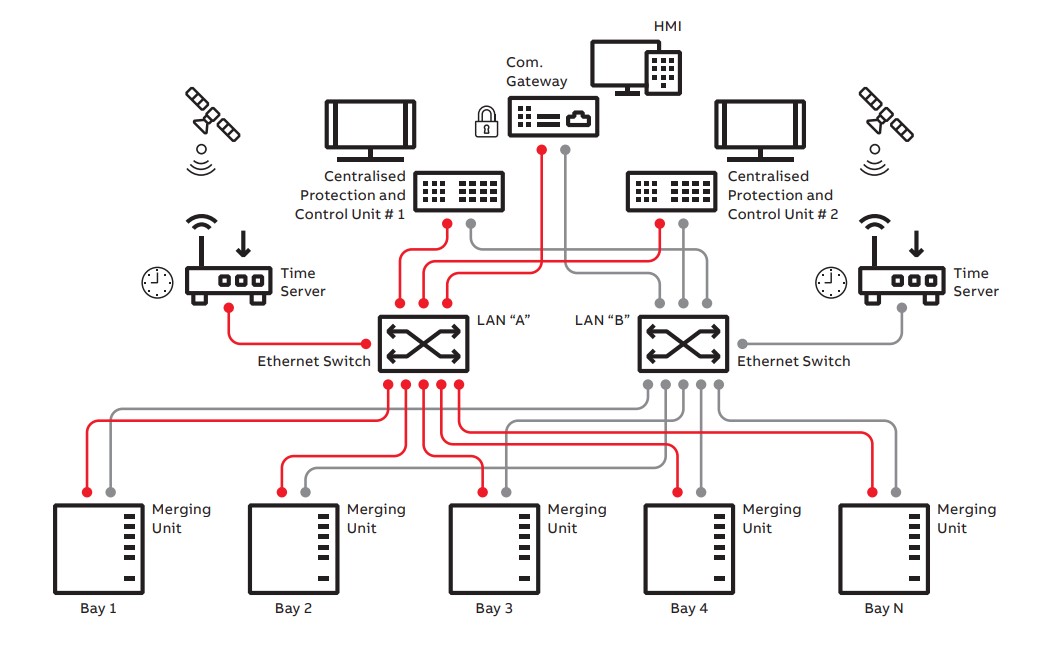
Most VPR systems are built around the IEC 61850 standard, which defines how protection and control data is exchanged over Ethernet networks. Key IEC 61850 services include:
- Sampled Values (SV) – Used to transmit real-time current and voltage measurements from merging units to protection software.
- GOOSE (Generic Object Oriented Substation Event) messaging – Used for ultra-fast exchange of critical signals, such as trip commands, between protection functions.
- MMS (Manufacturing Message Specification) – Used for supervisory control and data acquisition (SCADA), configuration, and monitoring.
Accurate timing is just as important as fast communication. Precision Time Protocol (PTP), defined by the IEEE 1588 standard, provides precise clock synchronization across devices on a local area network. PTP keeps merging units, protection algorithms, and control systems tightly synchronized in time, so that all decisions are based on a consistent and accurate view of the power system.
5. Redundancy and Failover
Because protection systems are mission-critical, VPR architectures are designed with redundancy at multiple levels. Virtual protection instances can run in parallel so that if one instance or component fails, another can immediately take over with no interruption to protection.
In many implementations, multiple VPRs perform the same protection function at the same time. If one instance stops responding due to a software fault, hardware issue, or network problem, the healthy instance continues operating seamlessly.
At the network level, redundancy is often achieved using the Parallel Redundancy Protocol (PRP), defined in IEC 62439-3. PRP provides zero-recovery-time Ethernet redundancy by sending duplicate data frames over two completely separate physical networks, commonly referred to as LAN-A and LAN-B.
Each device receives both copies of every message and uses the first one that arrives, discarding the duplicate. If a cable, switch, or entire network path fails, communication continues over the remaining network with no switchover delay and no data loss. This instant failover capability is essential for protection applications where even brief communication interruptions are unacceptable.
6. Testing & Simulation
Testing is a critical part of any protection system, and virtualized architectures make this process significantly more flexible. Before a VPR is deployed in a live substation, its behavior can be verified using digital twins and simulation environments.
A digital twin is a virtual replica of a physical device or system. By creating an accurate software model of protection relays, power equipment, and network behavior, engineers can simulate real-world operating conditions without needing the actual hardware. This allows protection logic to be tested under normal operation, fault conditions, and extreme scenarios in a controlled environment.
Through simulation, engineers can analyze performance, validate settings, and predict how the protection system will respond to disturbances. Issues can be identified and corrected early, reducing commissioning time and minimizing risk once the system is placed into service.
Summary
Virtual Protection Relays represent a natural evolution of grid protection, driven by advances in computing, networking, and software architecture. Rather than relying on dedicated hardware for each protection function, VPRs shift protection intelligence into software running on shared, high-performance infrastructure. While the form factor has changed, the fundamental protection principles remain the same.
By breaking the architecture down layer by layer, it becomes clear that a VPR is not a single piece of software, but a carefully integrated system. Robust hardware platforms provide the foundation, virtualization enables efficient resource sharing, and protection software implements time-tested algorithms. Communication standards such as IEC 61850 and IEEE 1588 ensure data moves quickly and remains synchronized, while redundancy and failover mechanisms maintain protection even during failures.
Testing and simulation complete the picture by allowing engineers to validate system behavior before deployment. Digital twins and virtual test environments reduce risk, shorten commissioning time, and make it easier to evaluate system performance under conditions that would be difficult or unsafe to recreate in the field.
References
- Virtual Protection Relays Explained
- Are Virtual Protection Relays the Future of Protection and Control?
- Virtual Protection Relays
- Virtualized Centralized Protection and Control Case Study
- Protection Relay Testing in Digital Twin
- IEC 61850
You may also like...
- Optimizing Infrared Scans: 5 Key Elements for Comprehensive Reporting
- SF6 Gas Alternatives for a Sustainable Energy Future
- Spotting Electrical Problems Before They Become Serious: A Standards-Based Approach
- Projects focused on renewable energy optimization are poised to disrupt the traditional marketplace
- Electrical Maintenance: Where Do I Start? How to Craft an Effective Testing Program
